Introduction to Bypassing SSL Pinning in Android APKs
In the ever-evolving landscape of mobile security, SSL pinning has become a crucial mechanism to safeguard sensitive data during transmission. Android applications commonly use SSL pinning to ensure that the app only communicates with trusted servers by validating their SSL certificates. This layer of security helps prevent man-in-the-middle (MITM) attacks, where attackers intercept and potentially manipulate the data exchanged between the app and its server.
However, for penetration testers, ethical hackers, or security researchers, bypassing SSL pinning becomes essential during application security assessments. This process allows experts to inspect network traffic, identify vulnerabilities, and ensure robust protection against malicious actors. While this technique is critical for security research, it also demands responsibility, as it should only be used within legal and ethical boundaries.
In this blog, we’ll explore the concept of SSL pinning in Android applications, why bypassing it is necessary for security testing, and various techniques to achieve it. From tools like Frida and Xposed to reverse engineering APKs, we’ll dive into the practical steps and challenges involved. Whether you're a security enthusiast or a professional tester, this guide will help you understand the nuances of SSL pinning bypass in Android apps.
Disclaimer: This information is intended solely for educational and ethical purposes. Always obtain proper authorization before testing any application. Misuse of these techniques may result in legal consequences.
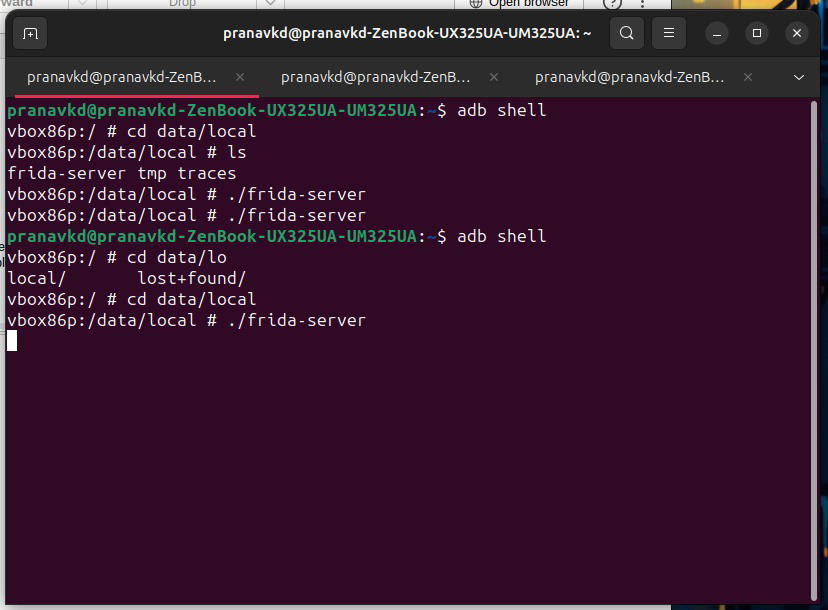
Step1. Install Frida and Objection In Our PC
install frida and objection by running this commands
pip install frida
pip install frida-tools
pip install objection
hellofind frida version by running command frida -v and note the version to download frida server from here